Overview
This article provides a comprehensive guide on configuring AD FS 3.0 on Windows Server 2012 R2 for SAML federation with Okta. It covers the prerequisites, configuration steps, and claim rules necessary for successful integration.
Information
This guide focuses on setting up AD FS 3.0 on Windows Server 2012 R2 to work with SAML federation. It includes detailed steps for creating a Relying Party Trust and configuring the required claim rules.
AD FS will be used in combination with a SAML federation in that version. Prefer an OIDC federation in newer versions.
|
OICD Federation (Metadata) |
https://sso.questback.com/FederationMetadata/2007-06/FederationMetadata.xml |
Prerequisites
-
The Server has to be part of the target Active Directory Domain
-
The Server Role “Active Directory Federation Services” has to be installed and configured on the server.
-
The three parts “Install a server SSL certificate”, “Install the AD FS server role” and “Configure the federation server” under Step 2 of the Microsoft documentation are quite helpful.
|
Microsoft Documentation |
There is no further configuration needed in AD FS to enable SAML authentication.
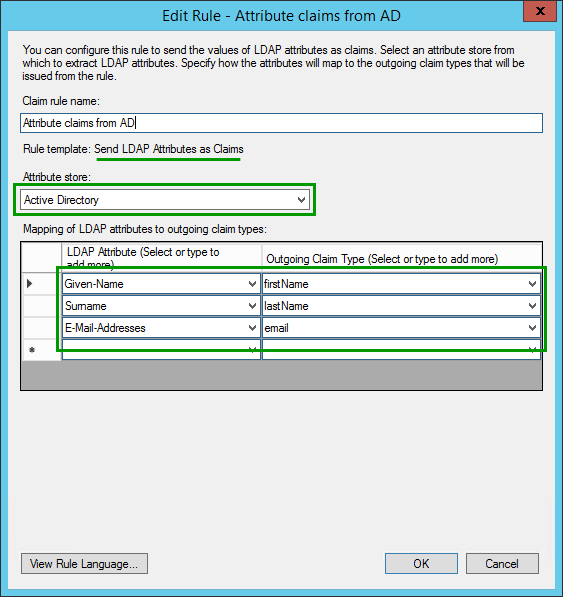
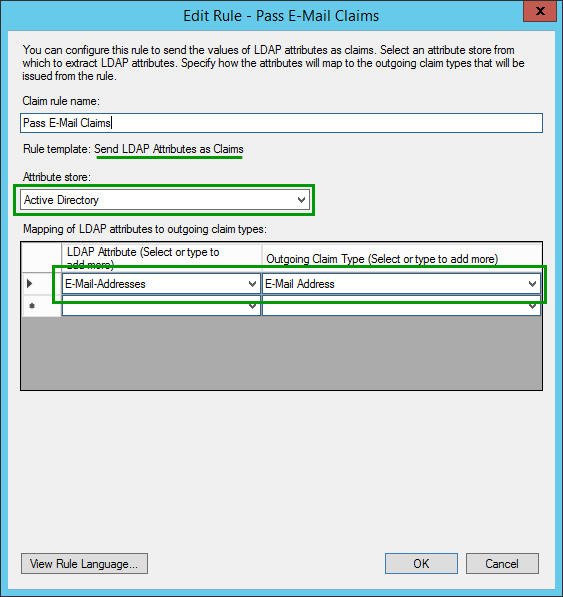
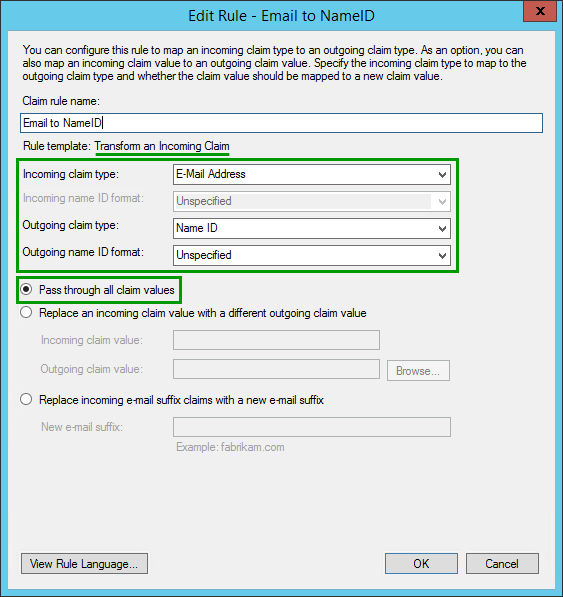
To successfully create a SAML federation between AD FS and Okta there are a few fields that are required by our Okta solution. The AD FS has to provide an email address, first name, and last name as well as an email address as NameID.
Configuration in AD FS
The steps might change with regard to the version and server version. They might also change with respect to the specific fields that are available in the actual AD FS instance.
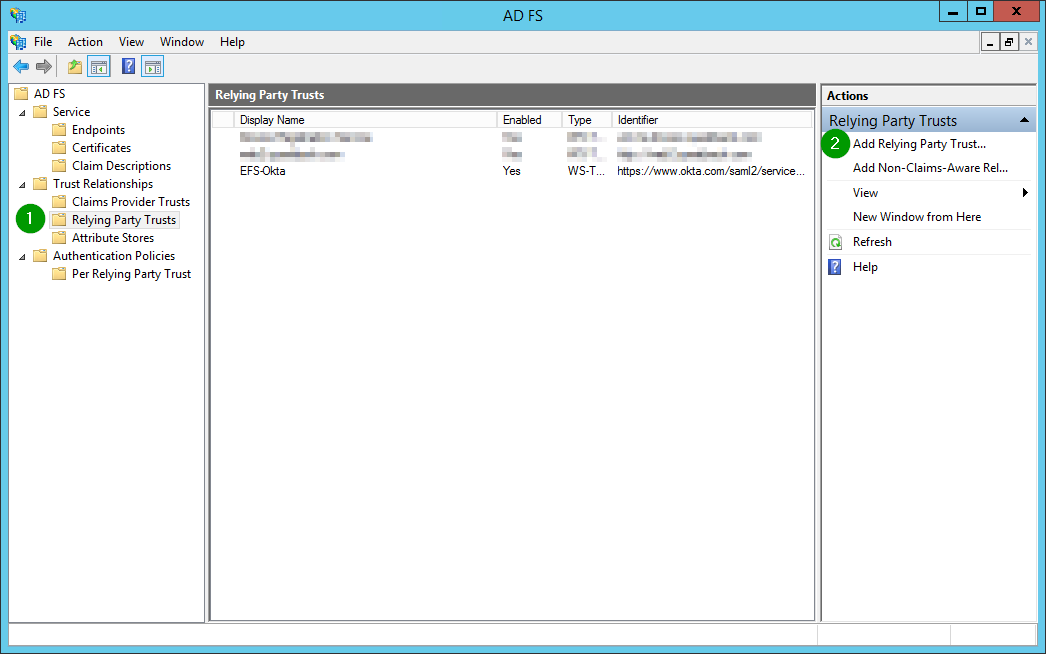
Step 1: Create a Relying Party Trust
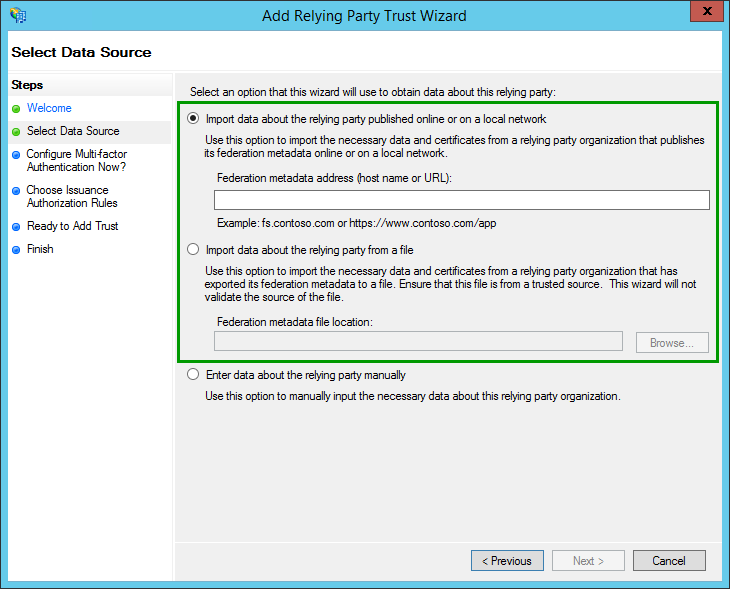
In the second step of the configuration wizard, the information can and should be imported via a metadata.xml file provided by Okta. This contains all the information needed to complete the wizard.
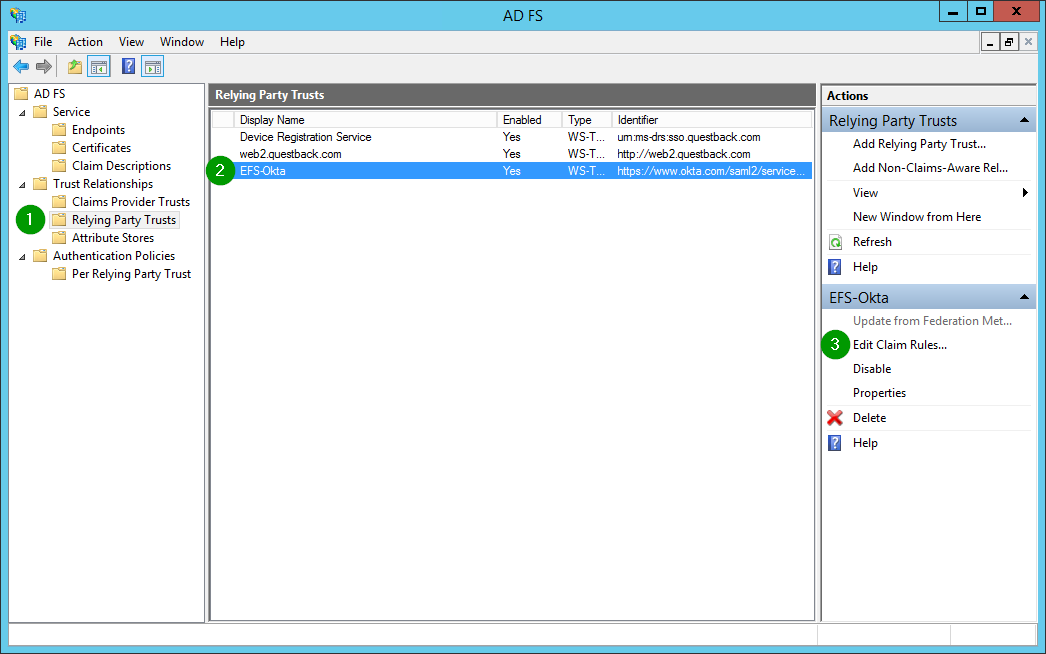
Step 2: Create Claim Rules
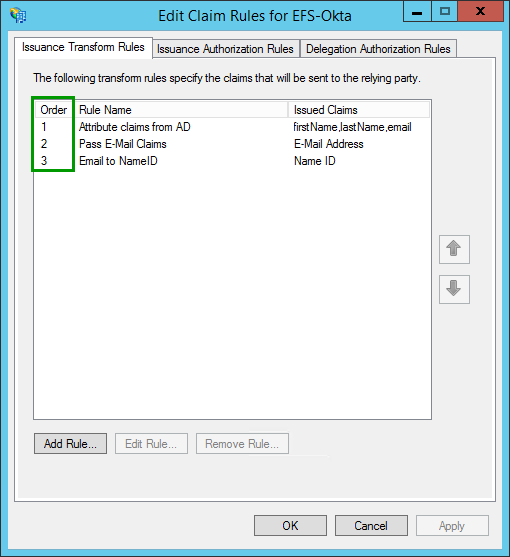
All claim rules for the formerly created Party Trust can be found here:
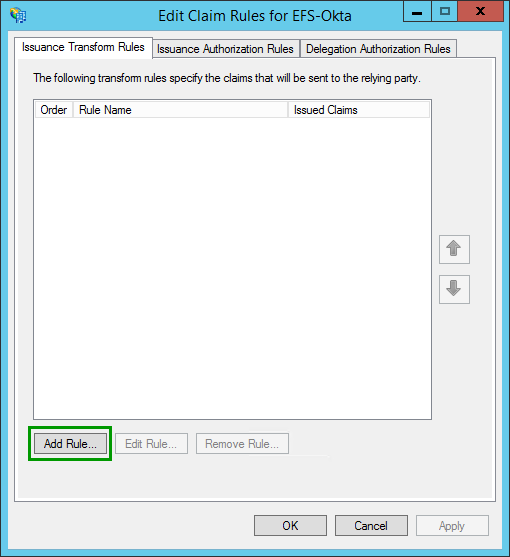
New rules can be created by clicking on “Add Rule…”:
The following three rules have to be created:
-
Attribute claims from AD
-
Pass E-Mail Claims
-
Email to NameID
Step 3: Check the order of the claim rules (important!)
FAQ
What version of AD FS is covered in this guide?
This guide covers AD FS 3.0 on Windows Server 2012 R2.
Is additional configuration needed in AD FS for SAML authentication?
No, there is no further configuration needed in AD FS to enable SAML authentication beyond what is described in this guide.
What information does AD FS need to provide for Okta integration?
AD FS needs to provide email address, first name, last name, and an email address as NameID for successful integration with Okta.
Priyanka Bhotika
Comments