Overview
This article explains the Content Security Policy (CSP) header in EFS, its purpose, and how to configure it for panel websites and surveys.
Information
The Content Security Policy (CSP) header is a security feature that controls which sources are allowed to load resources in a web application. This guide covers the default CSP settings in EFS, how to modify them, and best practices for implementation.
- What is Content Security Policy (CSP)?
- Default CSP in EFS
- Modifying CSP for Panel Websites and Surveys
- Example CSP Configurations
- Best Practices and Additional Information
What is Content Security Policy (CSP)?
Content Security Policy (CSP) is a security header that tells the browser which sources are allowed to load resources. In EFS, the default CSP only allows resources hosted on the EFS installation itself to load.
Default CSP in EFS
By default, EFS sends a CSP header that restricts resource loading to the EFS installation. This means that if custom code attempts to load additional resources from external sources (e.g., https://www.googletagmanager.com/), the browser will prevent these resources from loading when opening the panel website or survey.
Modifying CSP for Panel Websites and Surveys
For Panel Websites
To modify the CSP for panel websites:
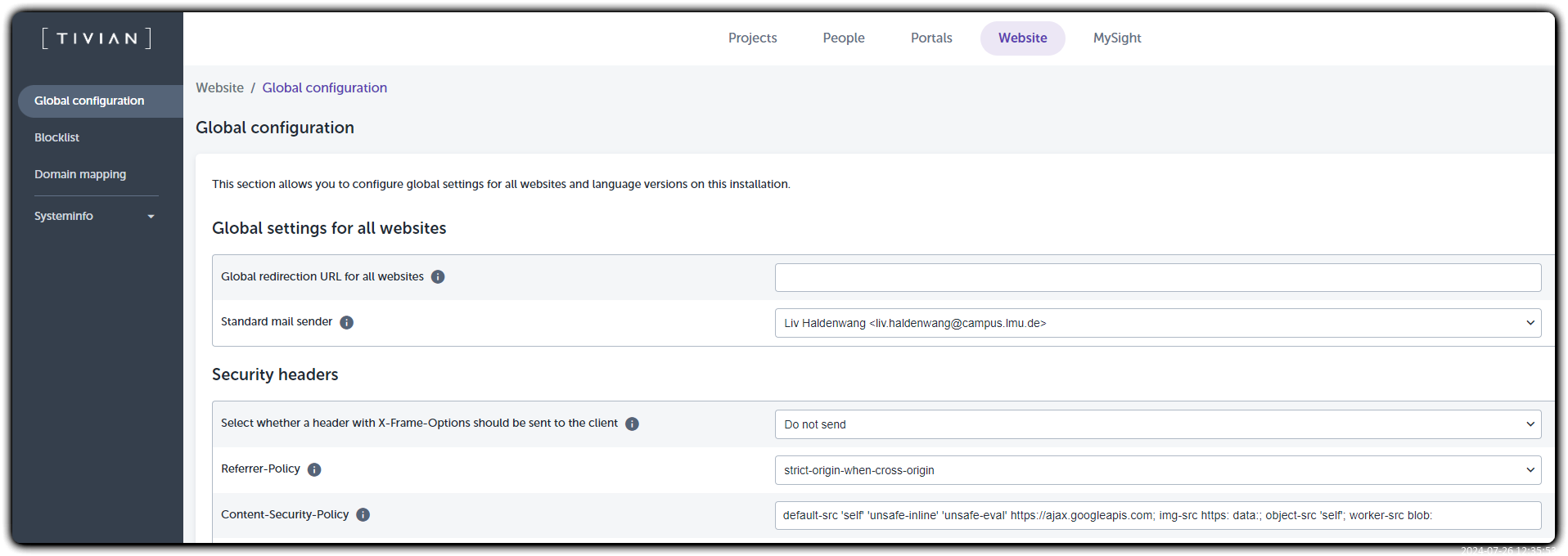
- Navigate to Website > select website from list > Global configuration
- Locate the "Content-Security-Policy" field
- Enter the desired CSP configuration
For Surveys
To modify the CSP for surveys:
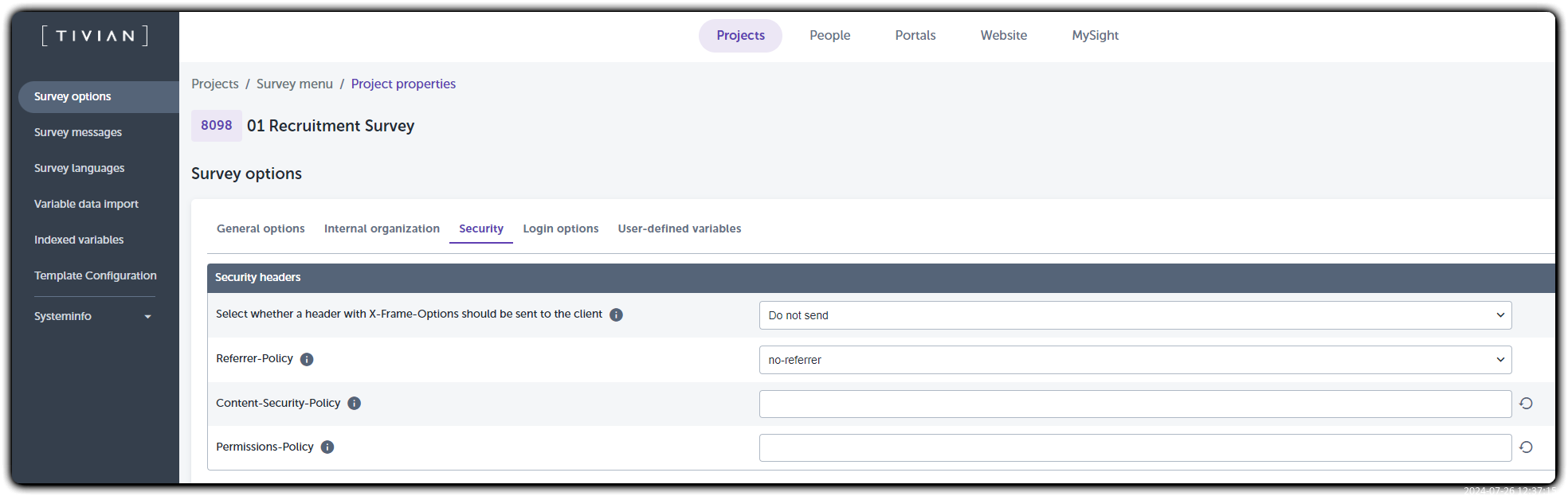
- Go to Survey menu > Project properties > Survey options > Security
- Find the "Content-Security-Policy" field
- Enter the desired CSP configuration
Example CSP Configurations
Default Content-Security-Policy
default-src 'self' 'unsafe-inline' 'unsafe-eval' https://ajax.googleapis.com; img-src https:; object-src 'self'
Example of Required Content-Security-Policy
default-src 'self' 'unsafe-inline' 'unsafe-eval' https://ajax.googleapis.com https://www.googletagmanager.com https://region1.google-analytics.com; img-src https:; object-src 'self'
Best Practices and Additional Information
While it's possible to leave the Content-Security-Policy field empty, which would allow all sources, this is not recommended from a security perspective. It's best to explicitly define allowed sources in the CSP.
For more detailed information on Content Security Policy, refer to the Mozilla Developer Network documentation: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy
FAQ
What happens if I don't set a Content Security Policy?
If you leave the Content-Security-Policy field empty, EFS will not send a CSP header, and all sources will be allowed to load. However, this is not recommended from a security standpoint.
Why does my custom code fail to load external resources?
If your custom code is trying to load resources from external domains not specified in the CSP, the browser will block these resources. You need to update the CSP to include these external domains explicitly.
Can I use different CSP settings for different surveys?
Yes, you can set different CSP configurations for each survey by modifying the "Content-Security-Policy" field in the survey's security settings.
Priyanka Bhotika
Comments